Last time, we talked through six user stories across three personas in IT Asset Management. Today, I’ll walk through what jumped out at me — please comment with your thoughts and considerations — there’s a lot going on here.
Blog

Better Security through Solid UX 3: Another example
Consider the following user stories for managing IT Assets in the CMDB. Next week, we’ll unravel common threads, opportunities, and potential fixes.

Better Security through solid UX 2: An example
We extend the principles of User Experience to a practical example: authenticating to a CRM.

Better Security through solid UX
This week we dial up the crazy: If you want to improve perception of your team, put some real energy into improving user experience.
Security Marketing and Sales, Part 2: Baggage
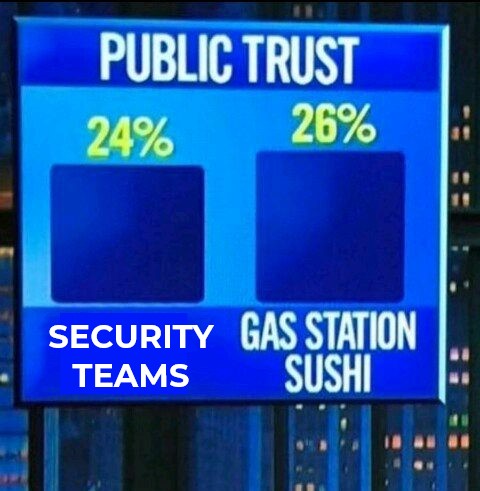
Today, I expand on the challenges most security leaders face when explaining the value of security: usually people already don't like you. We discuss what you can do about it, focusing on how you can make your services and platforms support your message of helpfulness.

Security Marketing and Sales
Today, I explore strategies to explain the value of security. This will be a key pre-requisite in credibly pushing your organization toward standard solutions. Luckily, there are already best practices in this space: educating people about value at scale is called Marketing and educating them about value individually is called Sales.

Security Is Not Job 0
I am here to tell you now as a seasoned professional: security is not that important. The lie is tempting, and thematically similar to a lie common across cultures and topics: if everyone was like me, they would be a lot better off.

CIS 2.3 - Unauthorized Software
The biggest risk from software is vulnerabilities and packaged malware. CIS 2.3 tells you to get rid of the worst stuff.

CIS 2.4 - Discovery
The biggest risk from software is vulnerabilities and packaged malware. The best way to start addressing that is to know what software is out there.
The 5 Types of Work
10 years ago, The Phoenix Project took the IT world by storm. It spoke to the deep dysfunction in many teams, of a million departments blamed for when things go wrong but never credit when things go right.
Why CIS
The Critical Security Controls (CIS, aka CIS Top 20) is a great framework. Many other people think so too; it’s exploded in popularity in the last 10 years. There are 4 big reasons why.
CIS 2.1 - the Mission
CIS 2.1 contains the core mission of CIS 2: have an accurate Software Inventory. The other CIS 2 controls are just supporting ways that help deliver that core mission.
CIS 2 Explained
An Inventory of IT Stuff is a helpful thing: it's a necessary starting point for lots of other technical security work. But you know what would be even more helpful? Knowing what each thing does. Zowie! That would be wild.
CIS 13.9 - NAC
CIS 13.9 is heavy. It requires big investments in the most expensive network gear, requires a fair amount of work to maintain, and can break systems if people make mistakes. It provides good protection from expert onsite attacks: nothing gets to talk unless it’s allowed.
CIS 1.3-5 - Discovery
CIS 1.3 - 1.5 use technical solutions to find all the IT Stuff for you, and report it back to your central inventory. They suggest three approaches, but there are bunches.
CIS 1.2 - Standard Work
There are several standard processes that most organizations will need to keep the inventory healthy and credible. Some can be integrated with existing processes, but none can be totally eliminated. CIS 1.2 proscribes the largest and most important kind of standard work: triage.
CIS 1.1 Part 2 - Useful Information
CIS 1.1 contains the core mission of CIS 1: have an accurate Inventory of IT Stuff. The other CIS 1 controls are just supporting ways that help deliver that core mission.
CIS 1.1 - the Mission
CIS 1.1 contains the core mission of CIS 1: have an accurate Inventory of IT Stuff. The other CIS 1 controls are just supporting ways that help deliver that core mission.
CIS 1 Explained
The CIS Controls say the most important thing to do to secure your computers is to have a list of all your stuff. They’re a little unclear by what this means and how it helps.
Troy Hunt on success
I enjoyed this recent piece by Troy Hunt, the celebrity creator of havibeenpwned. He departs from his usual technical topics, instead discussing the skills he's had to practice in the last year to stay effective while under more stress.
Telling a security story well - example #22
Cyentia offers consistently high-quality insights about the security value proposition. They recently did statistical analysis of major incidents in the last 10 years. Some highlights:
Sample CICD flow
At DevOpsDays KC, several people expressed interest in this CI/CD pipeline picture.
Agile in a Nutshell
Agile in a nutshell

